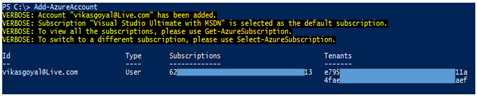
QUICK TIP : When you add your Azure account using PS Add-AzureAccount, you get subscription id and list of tenant IDs created in the subscription. The tenant IDs are actually related to Azure Active Directory tenants which you have created.
Friday, June 26, 2015
Friday, December 16, 2011
Free eBook on Claims based Identity and Access Control
Starts with discussing basics of claims based identity and moves to advanced topics.
Following industry standards are discussed :
- Security Assertion Markup Language (SAML)
- Security Association Management Protocol (SAMP)
and Internet Security Association
and Key Management Protocol (ISAKMP) - WS-Federation
- WS-Federation: Passive Requestor Profile
- WS-Security
- WS-SecureConversation
- WS-Trust
Wednesday, July 13, 2011
Whitepaper on exploit mitigation technologies
A new whitepaper has been recently published which discusses about various exploit mitigation technologies and how to use them. Release by Microsoft Security Engineering Center.
A must for every person on software development team. Covers following:
- economics of exploitation – attacker’s return on investment
- Tactics behind exploit mitigation technologies like enforcing variants, creating artificial diversity, leveraging knowledge deficits
- exploit mitigation technologies like
- Stack buffer overrun detection
- Data execution prevention (DEP)
- Address Space Layout Randomization (ASLR)
- SAFESEH and Structured Exception Handler Overwrite Protection (SEHOP)
- Heap metadata protection
- Enhanced Mitigation Experience Toolkit (EMET)
- For each technology it also mentions following:
- Overview
- How to use
- Proof point
- Performance consideration
- Compatibility considerations
- Availability on various OS/platforms including browser versions
Download the whitepaper from here http://www.microsoft.com/download/en/details.aspx?displaylang=en&id=26788
Friday, December 26, 2008
* Silverlight : Cross domain access guidelines
RIA (Rich Internet Applications) client runtimes like Silverlight and Flash does not allow any code to access cross domain sites unless the target sites specifically grant access. This is done to avoid issues like Cross-Site Scripting (XSS) attacks.
If you are involved in developing apps on Silverlight runtime, it helps to understand the runtime behavior for cross domain access both during development and deployment.
You can read my latest article on this:
Network Access from Silverlight and Cross Domain Access Guidelines
Tuesday, November 18, 2008
* Baking Security In
This is the new campaign from Microsoft to bring awareness about how MS products are made more secure and also releases tools and guidance as part of Security Development Lifecycle.
Catch all of it @ www.bakingsecurityin.com
Wednesday, November 05, 2008
* Windows Live ID to support OpenID
For users, Windows Live ID has provided a single credential to login into all Microsoft sites like MSDN, Connect, Live Mail etc. 
‘OpenID is an open, decentralized, free framework for user-centric digital identity. OpenID takes advantage of already existing internet technology (URI, HTTP, SSL, Diffie-Hellman) and realizes that people are already creating identities for themselves whether it be at their blog, photostream, profile page, etc. With OpenID you can easily transform one of these existing URIs into an account which can be used at sites which support OpenID logins.’
With Microsoft announcing the support of OpenID with Windows Live ID, now you can use the same Windows Live ID to login even on non-Microsoft sites which support authentication using OpenID. A test integration infrastructure is already live.
Get more details here : http://www.viawindowslive.com/Blog/LiveID.aspx
The production ready version is expected to go live in 2009.
Monday, November 12, 2007
* Agenda for Security Summit at Bangalore
In case you are still wondering what tomorrow's summit (Microsoft Security Summit) is going to offer to you .. here is the agenda :
0830hrs - 0915hrs : Registration
0915hrs - 1000hrs : Microsoft Security Strategy – An Update
1000hrs - 1100hrs : Security Trends in Today’s Operating Systems
1100hrs - 1130hrs : Software Updating: Hitting the Mark
1130hrs - 1145hrs : Tea Break
1145hrs - 1230hrs : Protecting sensitive data using encryption technologies
1230hrs - 1315hrs : Defense in Depth against malicious software
1315hrs - 1400hrs : Lunch
1400hrs - 1445hrs : Implementing Messaging & Collaboration Security
1445hrs - 1530hrs : Implementing network and perimeter Security
1530hrs - 1615hrs : Implementing security for Mobile device solution
1615hrs - 1630hrs : Tea Break
1630hrs - 1730hrs : Identity & access management : real world challenges & solutions
1730hrs – 1800hrs : Health Policy enforcement through NAP
Thursday, October 25, 2007
* Troubleshooting : Client Certificate Authentication
You are doing a setup for Client Certificate Authentication for your web application. The client and server tools involved are :
- Internet Explorer 6 or 7
- IIS 6.0
- Windows 2003
After installing client and server certificates and enabling 'Accept Certificates' at IIS end, you may face one of these problems:
- You are not able to verify whether the client certificate is currently installed for 'Client Authentication' in my browser because 'Intended purpose' doesn't show 'Client Authentication'
- When I try to access the site which accepts client certificates, I get a popup in browser to select the client certificate but it does not list my browser certificate.
Here are some things you can check:
- To get the 'Client Authentication' in 'Intended Purpose' drop down. Click 'Advanced..' button and uncheck 'Client Authentication'.
- Make sure that the CA of the client certificate is added to 'Trusted Root Certification Authorities' directory of web server machine. You can access this directory using 'Certificates' mmc snap-in.
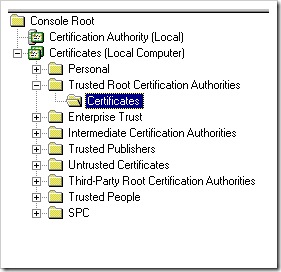
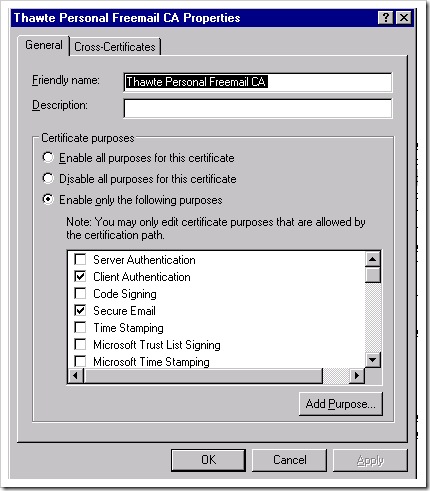
- Make sure the properties of the CA in same directory shows 'Client Authentication' as checked for Certificate Purposes.
Wednesday, October 24, 2007
* Security : Acrobat Reader flaw patched
Adobe has released the patch for the flaw detected earlier this month.
Saturday, October 13, 2007
* Security Alert : Adobe, Windows XP, IE 7
If you use Acrobat Reader on Windows XP machine with IE 7, you are at risk from malicious code and hacking attacks due to several security flaws in Acrobat products. This is I believe one of the most popular combination.
Ideally, like most of the companies, Adobe should have confirmed the flaw only after finding its fix, but it has already confirmed the flaw and fix is expected only by October end.
The workaround has been posted by Adobe at following url:
Monday, October 08, 2007
* Vulnerable Google Products
Recently lot of reports have surfaced exposing various kinds of Cross-Site Scripting (XSS) vulnerabilities in Google products.
The applications which have been found vulnerable are :
Government of India's agency Indian Computer Emergency Response Team recently issued an advisory for this issue.
Full report can be read here : Advisory for Google Users
Wednesday, September 19, 2007
* WCF : Hosting in Partial or Medium Trust ASP.NET environment
- Read about ASP.NET Partial Trust environment.
- Currently WCF provides very little support for partial trusted environment.
- When hosting in medium trust environment - only basicHttpBinding is supported by default. If you want to use wsHttpBinding, security mode needs to be set as 'None' or 'Transport'. Default security mode for wsHttpBinding is 'Message'.
- Partially trusted callers are currently not allowed to call WCF services.
* ASP.NET : Partial Trust Environment
ASP.NET runtime allows server administrators to configure runtime so that various asp.net applications can run in various levels of isolation and with various permissions.
- This is most relevant in shared hosting kind of scenarios.
- The various levels of trust available are : Full|High|Medium|Low|Minimal
- By 'Partial Trust' means, server admin trust the applications hosted in web server only partially and so applications cannot perform lot of low level functions and do not have access to lot of system resources.
- For each level the various kinds of restrictions are applied on applicaitons.
- "Full" trust means that applications are assumed to be fully trusted and so have full permissions and access to all system resources.
- These permission are independent of what Operating System allows applications to do.
- The trust level at machine level can be configured using machine level web.config.
<location allowOverride="true">
<system.web>
<securityPolicy>
<trustLevel name="Full" policyFile="internal" />
<trustLevel name="High" policyFile="web_hightrust.config" />
<trustLevel name="Medium" policyFile="web_mediumtrust.config" />
<trustLevel name="Low" policyFile="web_lowtrust.config" />
<trustLevel name="Minimal" policyFile="web_minimaltrust.config"/>
</securityPolicy>
<trust
level="Full"
originUrl=""
processRequestInApplicationTrust="true"
/>
</system.web>
</location>
- 'allowOverride' determines whether the machine level web.config can override the settings in machine level web.config. 'False' means NO.
- The permissions granted as part of various levels can be configured using the config files mentioned in <securityPolicy> section.
- Custom policies can also be created and registered.
- <trust> element can be used to configure the current level.
- So, when you deploy your applications in third party servers or production servers, make sure that you test your applications with their security configuration first.
- While these settings determine the permissions given to hosted applications in web server, they are independent of how your applications react to partial trusted callers.
- On broad level this is covered under 'Code Access Security' .
- By default under 'medium' level, the application cannot do any of the following :
-
Call unmanaged code.
-
Call serviced components.
-
Write to the event log.
-
Access Microsoft Message Queuing queues.
-
Access ODBC, OleDb, or Oracle data sources.
Monday, January 22, 2007
* How to build Authorization Module for TCP Remoting channel
From .NET 2.0, framework includes the security infrastructure for TCP channel which can be enabled just by configuration.
The below entry enables security for tcp channel
<configuration>
<system.runtime.remoting>
<application>
<service>
<wellknown mode="SingleCall" type="VikasGoyal.ImplementationClass, Server" objectUri="server.rem" />
</service>
<channels>
<channel ref="tcp" secure="true" port="8080" impersonate="true" />
</channels>
</application>
</system.runtime.remoting>
</configuration>
Apart from providing authentication support, centralized authorization hook has also been included which can be used to implement authorization on all connections made on the tcp channel.
The property added is authorizationModule. The sample below shows the usage :
<?xml version="1.0" encoding="utf-8" ?>
<configuration>
<system.runtime.remoting>
<application>
<service>
<wellknown mode="SingleCall" type="VikasGoyal.ImplementationClass, Server" objectUri="server.rem" />
</service>
<channels>
<channel ref="tcp" secure="true" port="8080" impersonate="true" authorizationModule="VikasGoyal.Server.AuthorizationModule, Server, Version=1.0.0.0, Culture=neutral, PublicKeyToken=null" />
</channels>
</application>
</system.runtime.remoting>
</configuration>
AuthorizationModule should implement System.Runtime.Remoting.Channels.IAuthorizeRemotingConnection interface which provides methods where authorization checks and decisions can be taken based on the client's network address and user identity.
Below is the sample implementation :
class AuthorizationModule : IAuthorizeRemotingConnection
{
public bool IsConnectingEndPointAuthorized(System.Net.EndPoint endPoint)
{
Console.WriteLine("Connecting IP: " + endPoint);
return true;
}
public bool IsConnectingIdentityAuthorized(IIdentity identity)
{
Console.WriteLine("Connecting identity: " + identity.Name);
return true;
}
}
Related Links